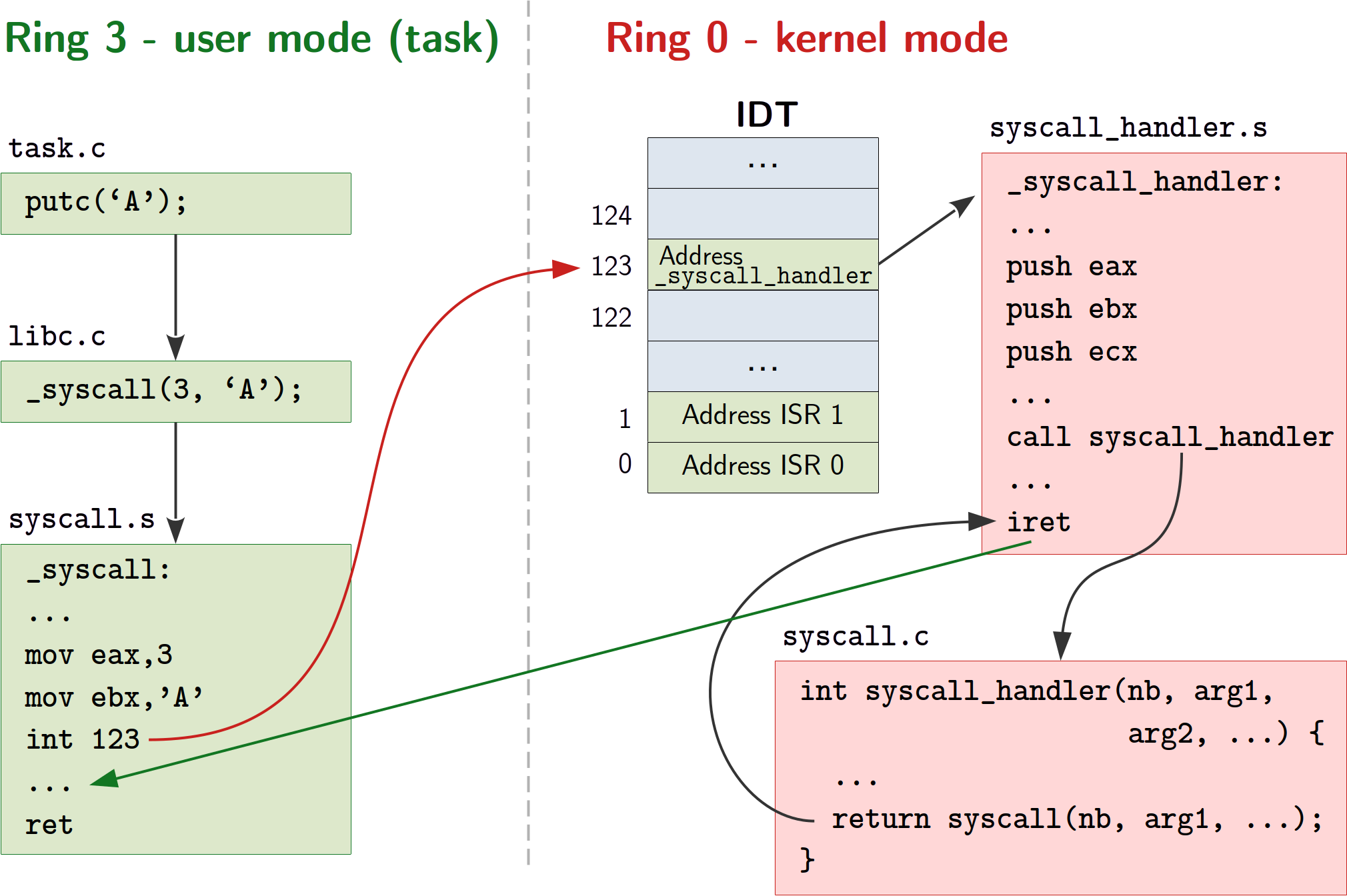
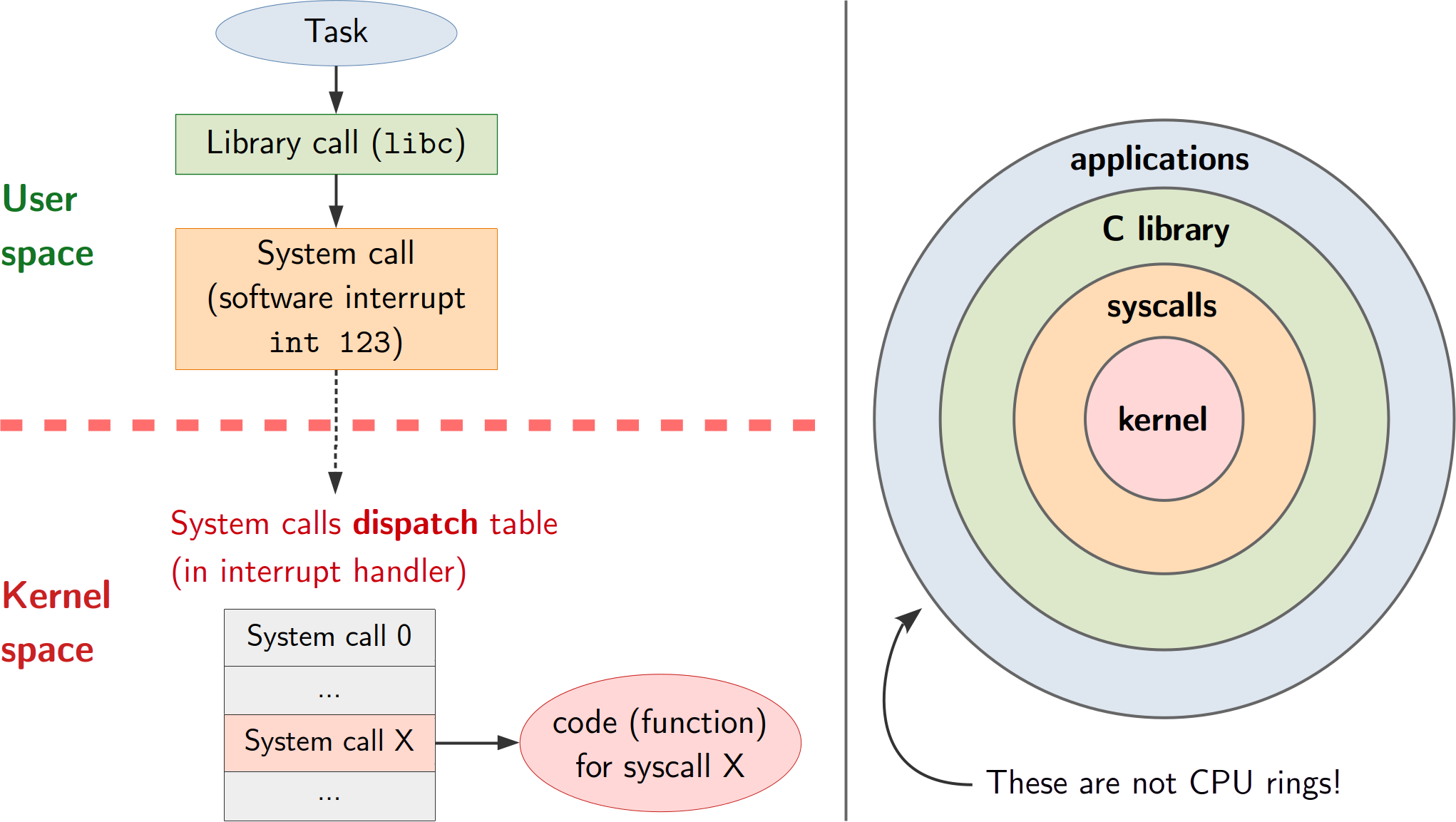
-
- Downloads
added 07-System_calls
Showing
- course/07-System_calls.md 326 additions, 0 deletionscourse/07-System_calls.md
- course/07-System_calls.pdf 0 additions, 0 deletionscourse/07-System_calls.pdf
- course/images/syscall_full_workflow.odg 0 additions, 0 deletionscourse/images/syscall_full_workflow.odg
- course/images/syscall_full_workflow.png 0 additions, 0 deletionscourse/images/syscall_full_workflow.png
- course/images/syscalls_dispatch_table.odg 0 additions, 0 deletionscourse/images/syscalls_dispatch_table.odg
- course/images/syscalls_dispatch_table.png 0 additions, 0 deletionscourse/images/syscalls_dispatch_table.png
course/07-System_calls.md
0 → 100644
course/07-System_calls.pdf
0 → 100644
File added
No preview for this file type
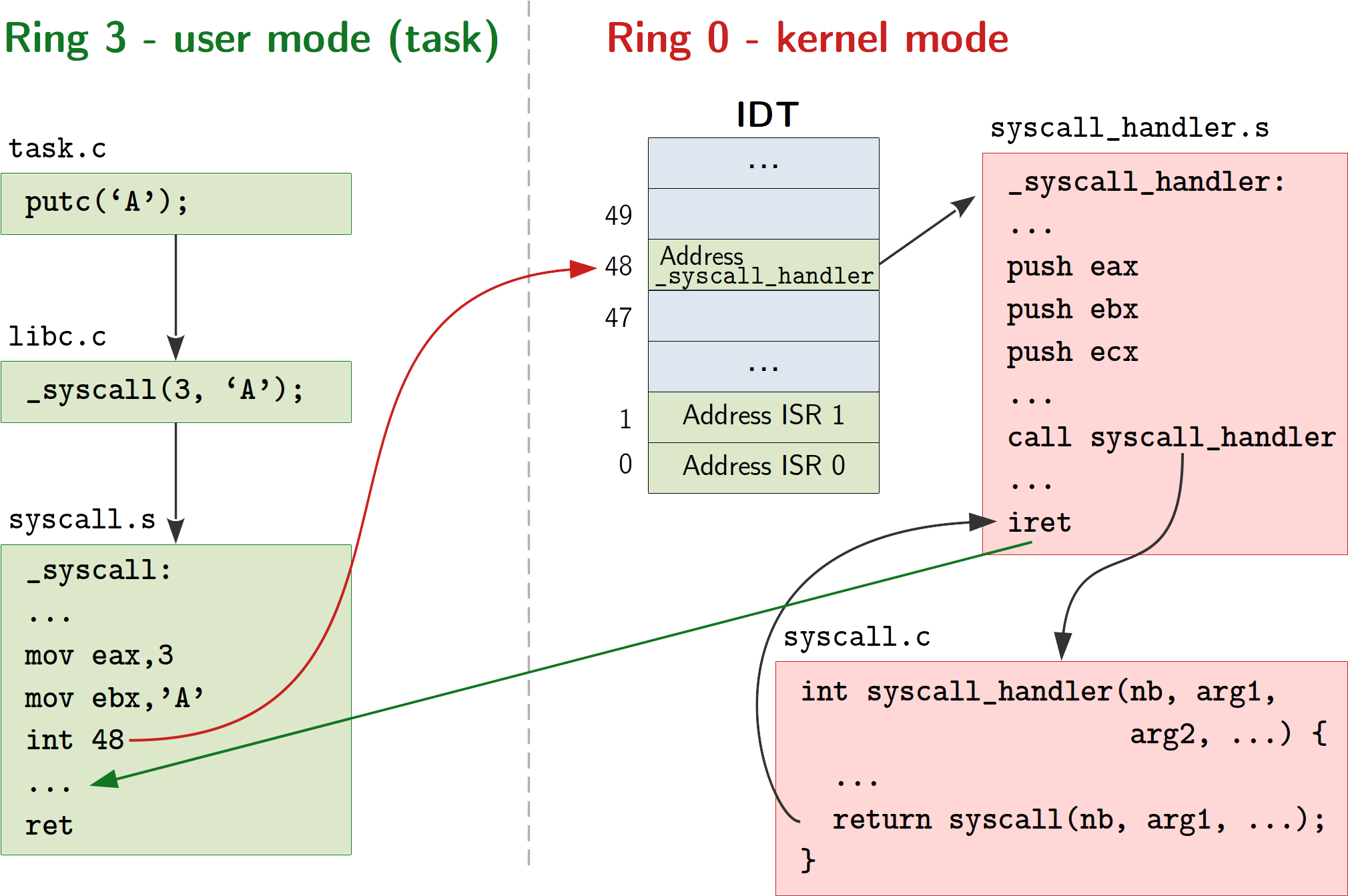
| W: | H:
| W: | H:


No preview for this file type
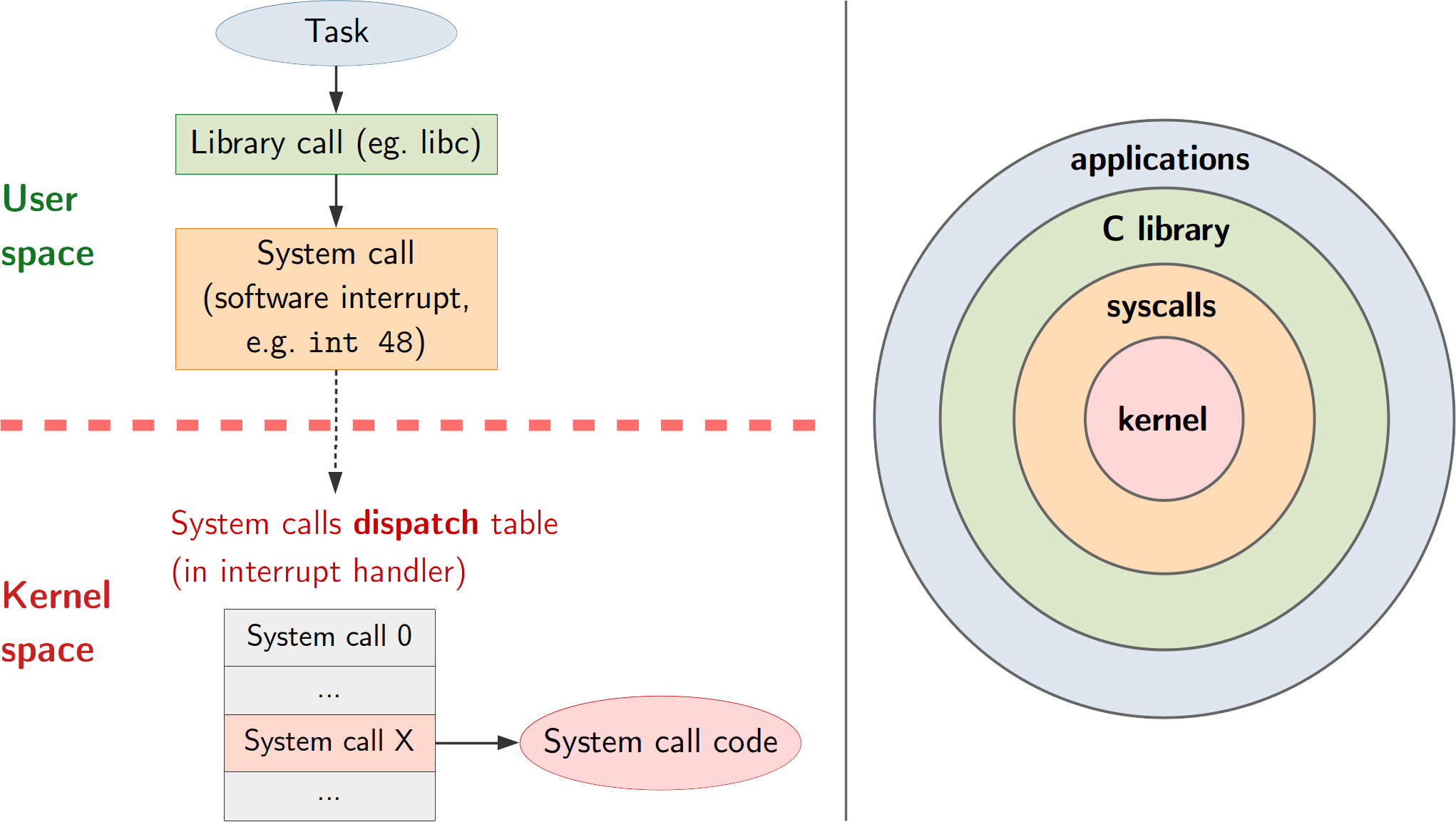
| W: | H:
| W: | H: